A virtual network is a logical representation of an isolated network in Microsoft Azure. VNet enables services in the Azure network to communicate securely with each other. It’s similar to a physical network which connects computers using hardware, whereas Azure virtual networking connects services across many locations and comes with inbuilt features like scalability, security, and high availability.
By default, all resources in Virtual Network can communicate outbound to the internet. However, we can use public IP addresses or a public load balancer for an inbound internet connection.
Components of Virtual Networking
Address Space:
Address Space is required to define the custom private address space (RFC 1918) range while creating a VNet resource. Microsoft Azure recommends below address spaces for private IP address communication:
- 10.0.0.0 – 10.255.255.255
- 172.16.0.0 – 172.31.255.255
- 192.168.0.0 – 192.168.255.255
Note: Make sure VNet address spaces cannot overlap each other.
Subnet:
Subnet plays a vital role in segmenting the virtual network into multiple networks to isolate the traffic and provides better security. A subnet can be defined as a range of IP addresses within the virtual network address space range. An IP defined in a subnet can communicate with other IP addresses configured within the VNet by default. However, we can customize this behavior using the Network Security Group.
NSG:
Network Security Groups (NSGs) are used in Azure Virtual Network (VNet) to provide an additional layer of network security by filtering inbound and outbound traffic based on specific protocols, ports, or IP addresses. NSGs help to segment the network traffic, monitor network activity, and customize security rules to meet business needs.
Interested in Document360 Knowledge base? Schedule a demo with one of our experts
Book A Demo
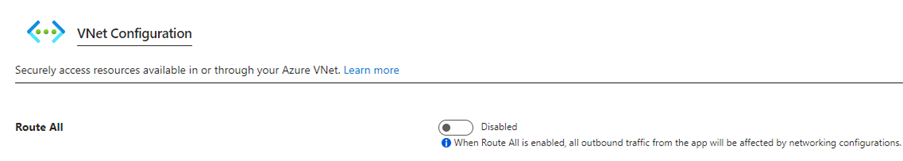
How does “Route All” impacts VNet?
In Azure Virtual Network (VNet), “Route all ” is a network routing option that directs all traffic in the VNet to the next hop. This means that any traffic originating from resources within the VNet will be sent to the specified next hop, which can be any configured Azure resources (Ex: Azure VM, Load Balancer, Application Gateway, or VPN Gateway).
The impact of using “Route all” in Azure VNet can be significant and should be carefully considered. below are some of the key considerations while designing the networking with route all options:
Network Performance:
“Route all” can affect network performance, as all traffic in the VNet is directed to the specified next hop. If the next hop is not properly sized or configured, it can become a bottleneck and cause performance issues.
Network Security:
It is possible to have an impact on network security. Since all traffic is directed to the next hop, it can be intercepted or redirected if the next hop is compromised. It’s important to ensure that the next hop is properly secured and monitored.
Routing Complexity:
It can make routing more complex, primarily if multiple next-hops are used for different types of traffic. This can make it harder to troubleshoot the network issues and can lead to possible routing conflicts if not properly configured.
Cost:
It can also have cost implications, as the next hop may be an Azure resource that incurs additional charges. It’s important to consider the cost of using “Route all” and to ensure that it is properly sized and configured to minimize costs.
How it helps Document360?
Isolation:
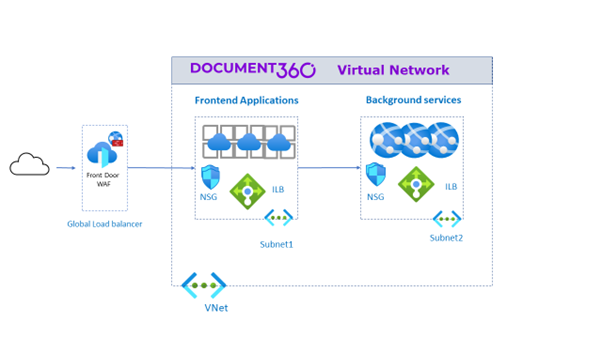
Document360 uses a dedicated Virtual Network for the services hosted in the cloud for better isolation and sophisticated network topologies.
Security:
VNet provides a secure environment and network for all our applications. Moreover, it provides reliable and excellent network connectivity. It provides an extra layer of security for our resources, as they are not directly exposed to potential threats.
Customization:
It gives us full control over network configuration to monitor the incoming/outgoing traffic and create the rules to allow or deny the traffic.
Scalability:
VNet is highly scalable; it allows us to easily add or remove resources based on business demands. We can also use Azure VNet peering to connect multiple VNets which enables us to scale out the network architecture without sacrificing performance.
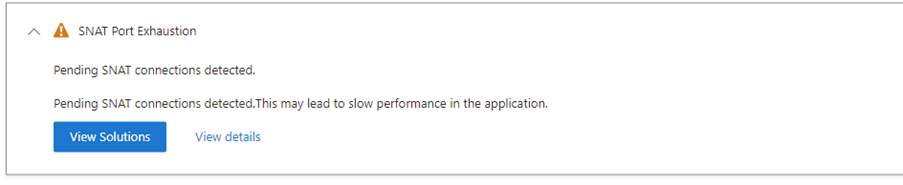
SNAT Port Exhaustion
Azure Web Apps or virtual machines may need to have outbound connectivity to the internet for certain use cases. This process uses source network address translation (SNAT) to translate the web application’s private addresses to the load balancer’s public IP address. Generally, Azure App Service web application needs to connect with different external applications/endpoints, such as Redis, Search Server endpoints SQL/NoSQL Databases, and call another RESTful service.
Every instance of Azure App service is initially pre-allocated with 128 SNAT ports. The SNAT port limit affects when every connection to the same destination IP and destination port uses a SNAT port.
SNAT port exhaustion occurs when the server runs out of available ports to use for translation.
Cost:
Azure VNet is a paid service, so it’s important to consider the cost implications of your network design. You can use Azure Cost Management and Billing to monitor your Azure usage and optimize your costs.
Also Read: How Document360 Leverages Azure AI to Elevate Knowledge Management
Conclusion
Azure Virtual Network is a powerful service that provides a secure and scalable way to connect your resources in the cloud. By carefully designing your network topology and considering factors such as IP addressing and security, you can create a customized network environment that meets your business needs. With Azure VNet, you can take full advantage of the cloud’s flexibility and agility while maintaining the security and control that your business requires.


 –
–